AWS Partner Network (API)
Overview
This guide walks you through setting up the AWS Partner Network (APN) integration using the Partner Central API.
With this integration, you can seamlessly sync opportunities, share referrals, and manage co-sell engagements with AWS.
Prerequisites
- Identity and Access Management (IAM) administrator
- handles permissions and technical setup in AWS (e.g. IAM roles, policies, or SSO).
- AWS Partner Central Alliance Lead or Cloud Administrator
- the primary account owner in AWS Partner Central, with authority to accept AWS Partner Network terms.
1. Link AWS Seller Account to APN
Step 1. Identify an AWS account to link
Before linking, your Alliance Lead (or Cloud Admin) and IAM Administrator should select the AWS account that will be connected to Partner Central.
- General recommendation
- AWS recommends linking an account dedicated to APN engagements.
- If your company has multiple AWS accounts, consider selecting the one that:
- You use to sign in to AWS Partner Central
- Represents your global business
- Serves as the primary account for administrative tasks
- If you are an AWS Marketplace seller:
- You may choose to link a Marketplace seller account.
- If you own multiple Marketplace accounts, select your primary account such as the one with the most transactions.
Step 2. Grant Access to Your Team
Before linking your AWS account, ensure that the right permissions are in place. This step is handled by your IAM Administrator.
- The IAM Administrator must configure IAM policies so that Partner Central users (Alliance Lead or Cloud Admin) have the necessary access to complete the account linking process.
- Follow the AWS official guide: Account Linking Prerequisites → Granting IAM Permissions for the latest instructions on which IAM policies are required.
In most cases, this involves granting read-only IAM permissions and allowing Partner Central to create the required roles (e.g., Cloud Admin, Alliance, ACE). We recommend letting your IAM Administrator review the official AWS guide to ensure compliance with your company’s security practices.
Step 3. Start the Linking Process
- Sign in to AWS Partner Central with an Alliance Lead or Cloud Admin role.
- On the homepage, click Link Account.
- Click Continue to Account Linking once Step 2 has been completed.
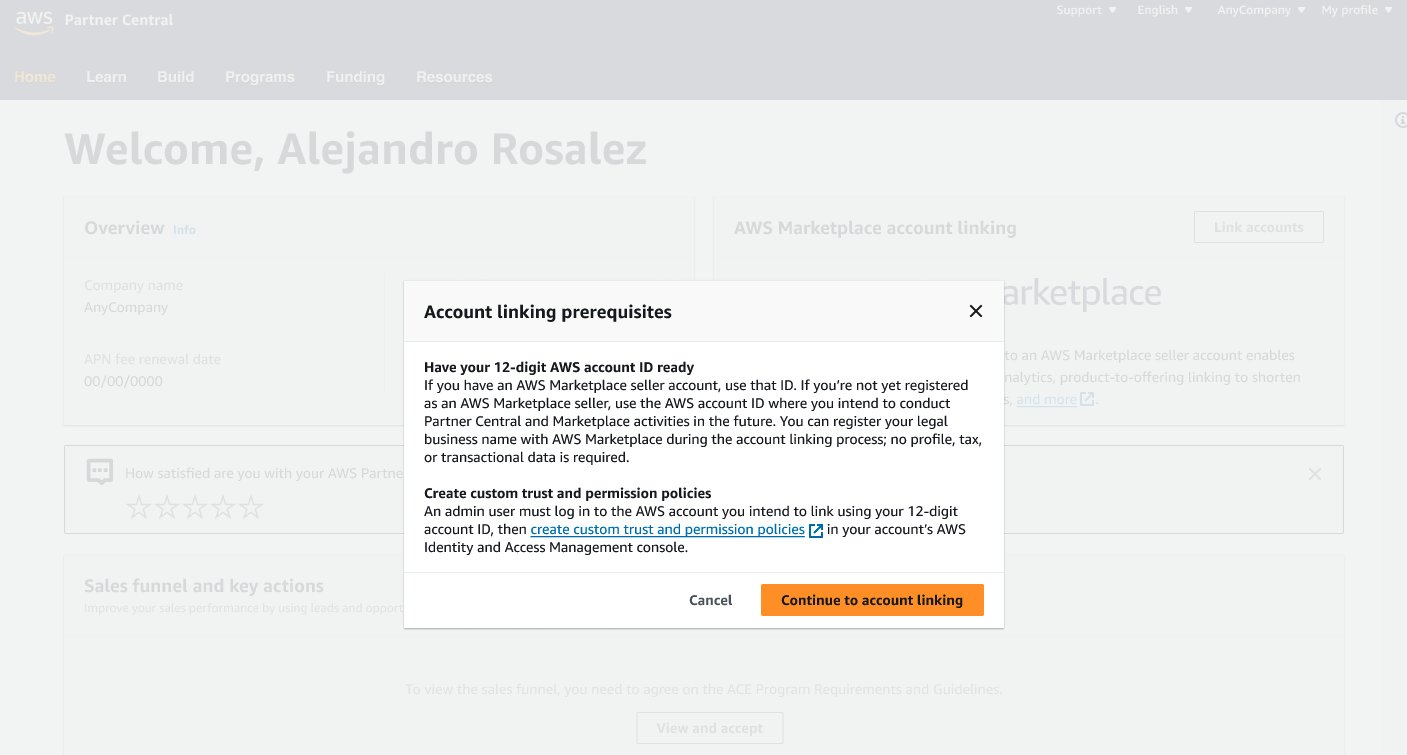
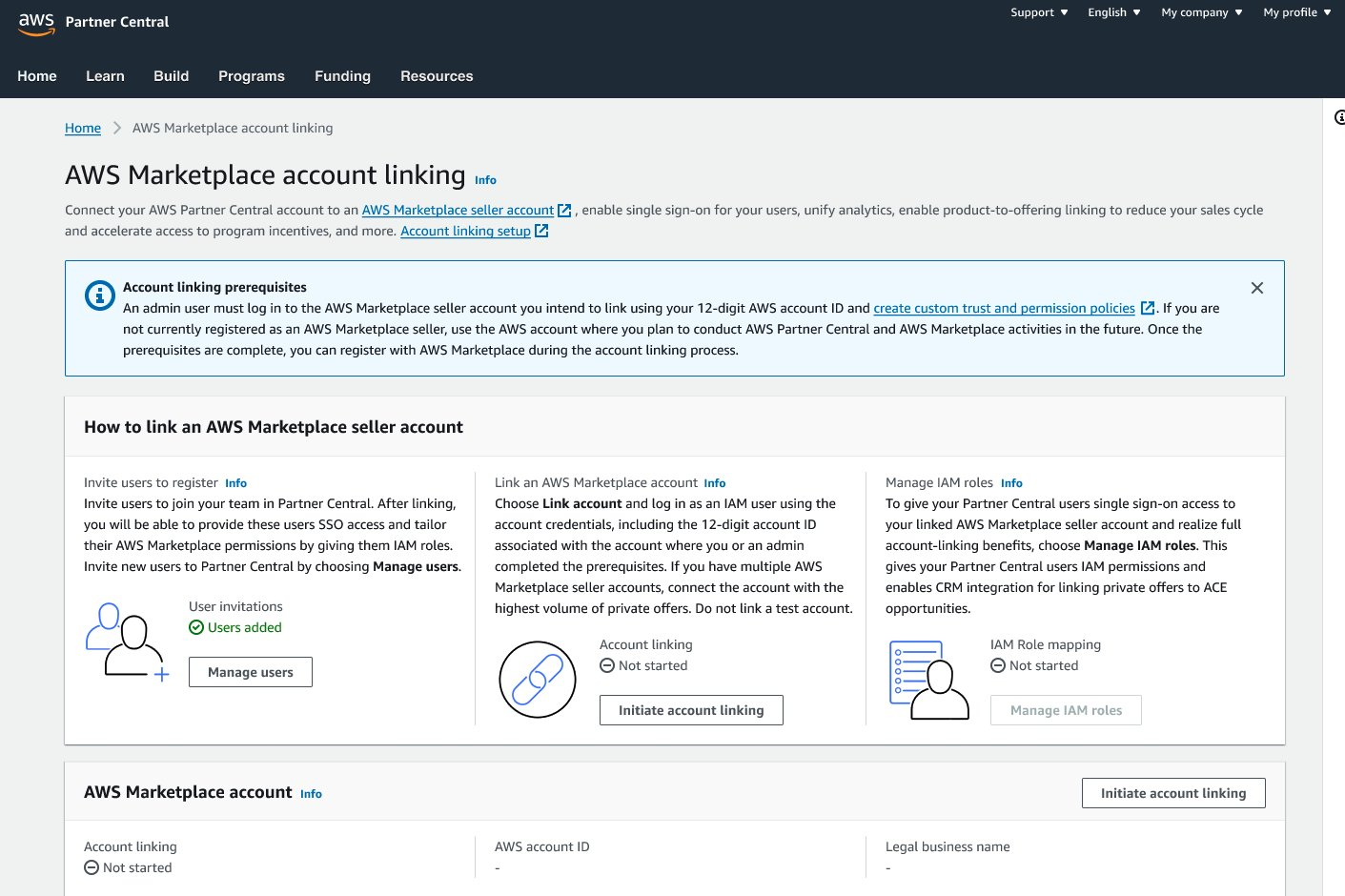
- Click Initiate Account Linking
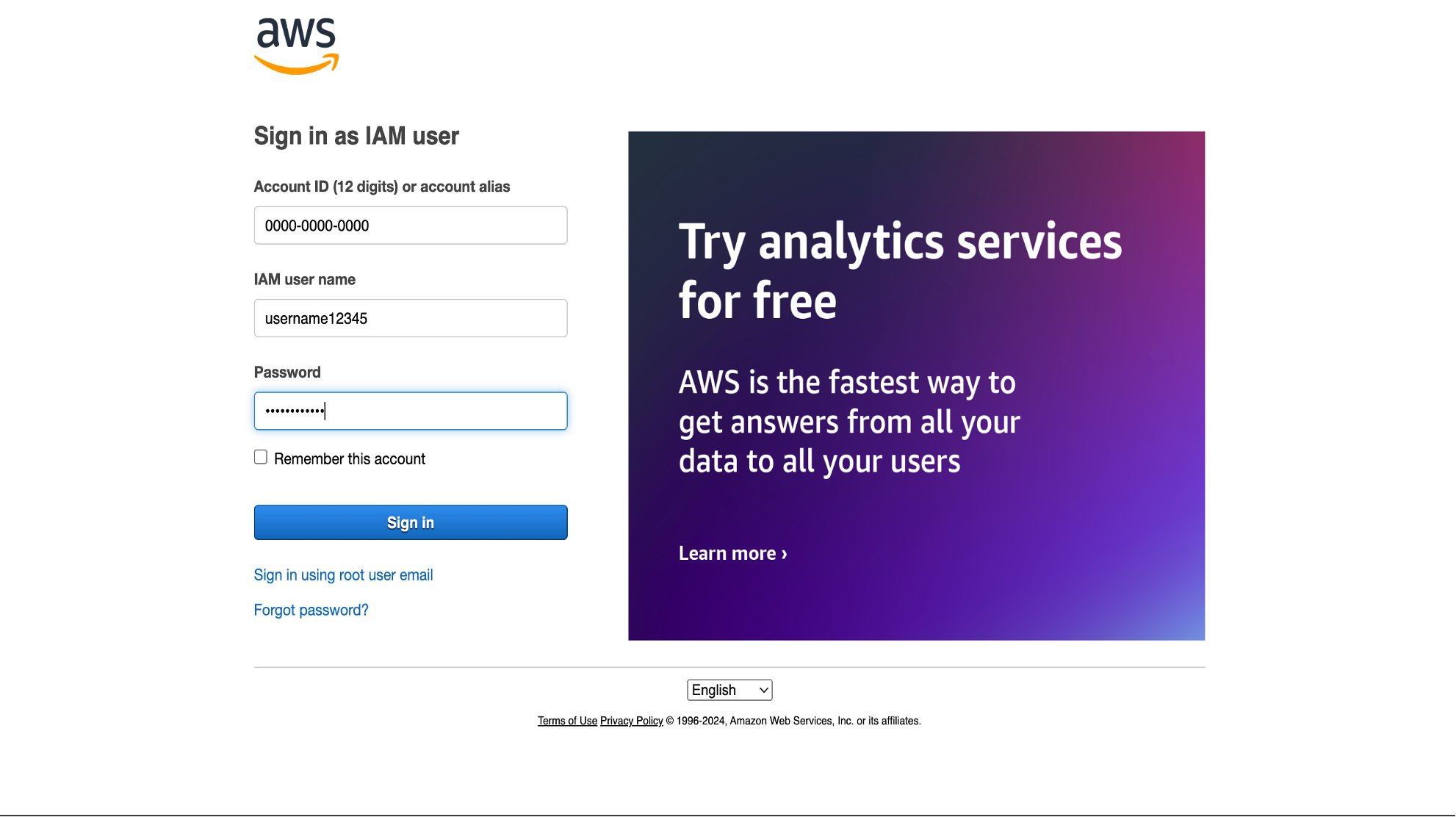
Step 4. Sign in to Your AWS Account
- Sign in with AWS account ID along with its IAM user name, and Password.
- If your organization uses single sign-on (SSO), use those credentials to sign in to your AWS account first, then sign in to AWS Partner Central.
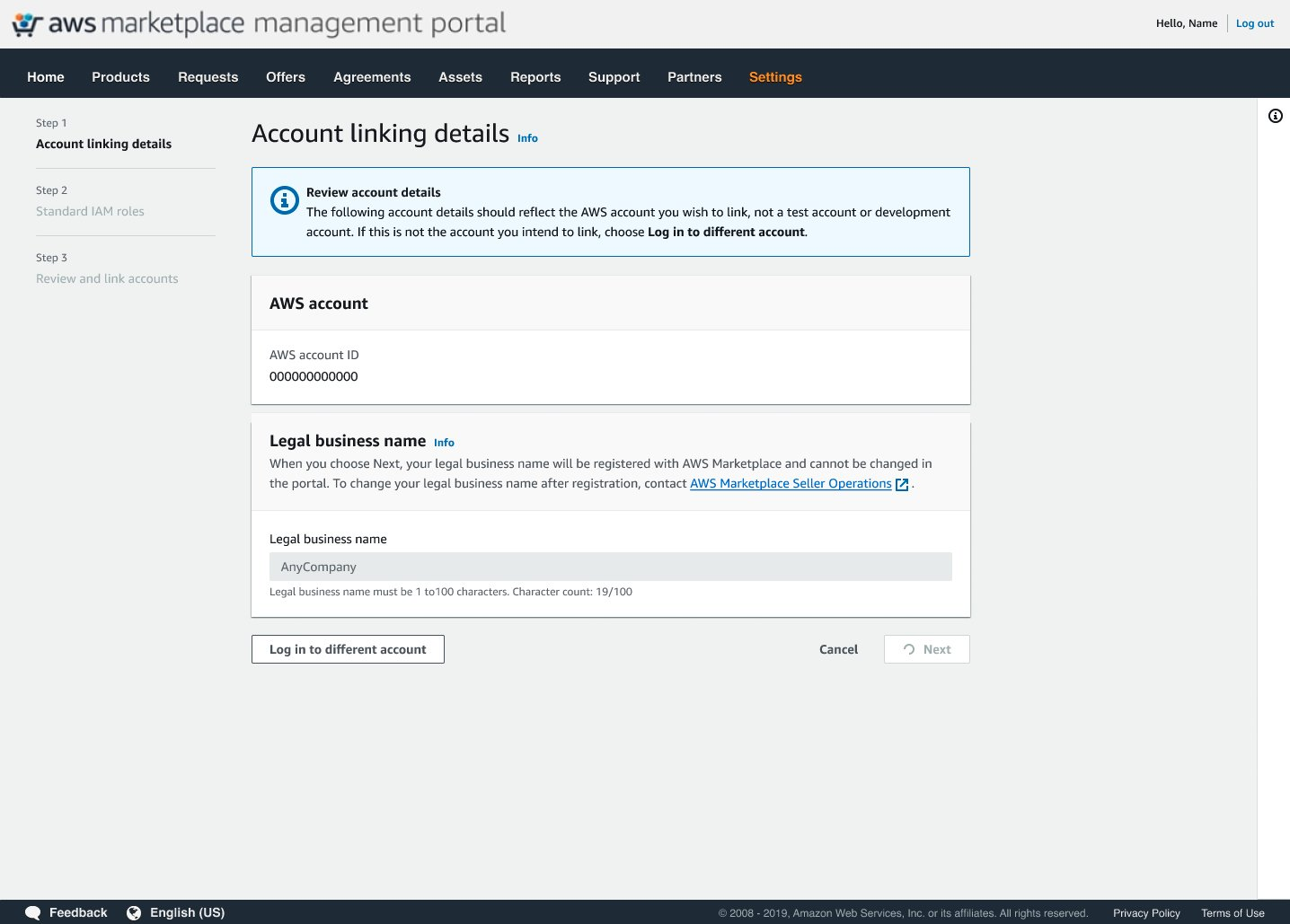
Step 5. Provide Legal Business Information
This step is required only if the selected account has not yet been registered as a Marketplace seller.
- Enter your Legal Business Name and click Next.
- Doing this will register your account as a seller in the background, but:
- Your account will not become public-facing.
- You will not be able to list products until you complete the full Marketplace seller registration process separately.
- Regional note: If your company is under AWS India (Amazon Web Services India Private Limited), you can skip this step and proceed directly by clicking Next.
Step 6. Assign IAM Roles
- (Recommended) Check all the boxes to assign IAM roles (eg. Cloud Admin, Alliance Team, and ACE team) to existing Cloud Admins, Alliance Team, and ACE users in AWS Partner Central.
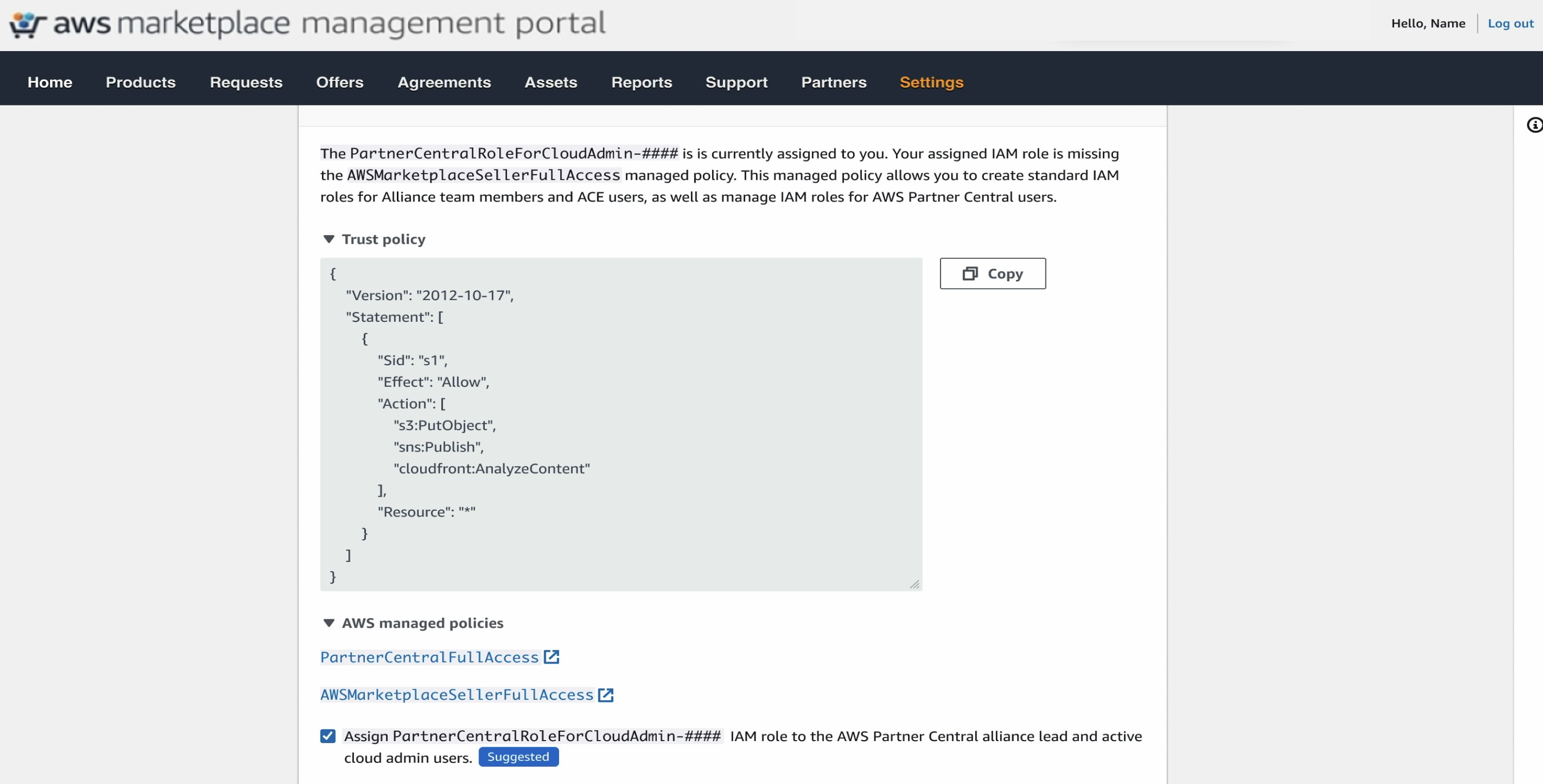
- This ensures that your Partner Central users have the correct permissions from the start. Bulk assignment vs. manual mapping: Bulk assignment is only available during the linking workflow. You can still assign or adjust IAM roles later, but it must be done manually after linking.
- Standard role creation: Cloud Admin, Alliance Team, and ACE Team roles are created automatically once the account is linked — even if you don’t assign them during this step.
- Role cleanup: If any roles are unnecessary, your IAM Administrator can remove them in the AWS IAM console.
- Click Next button.
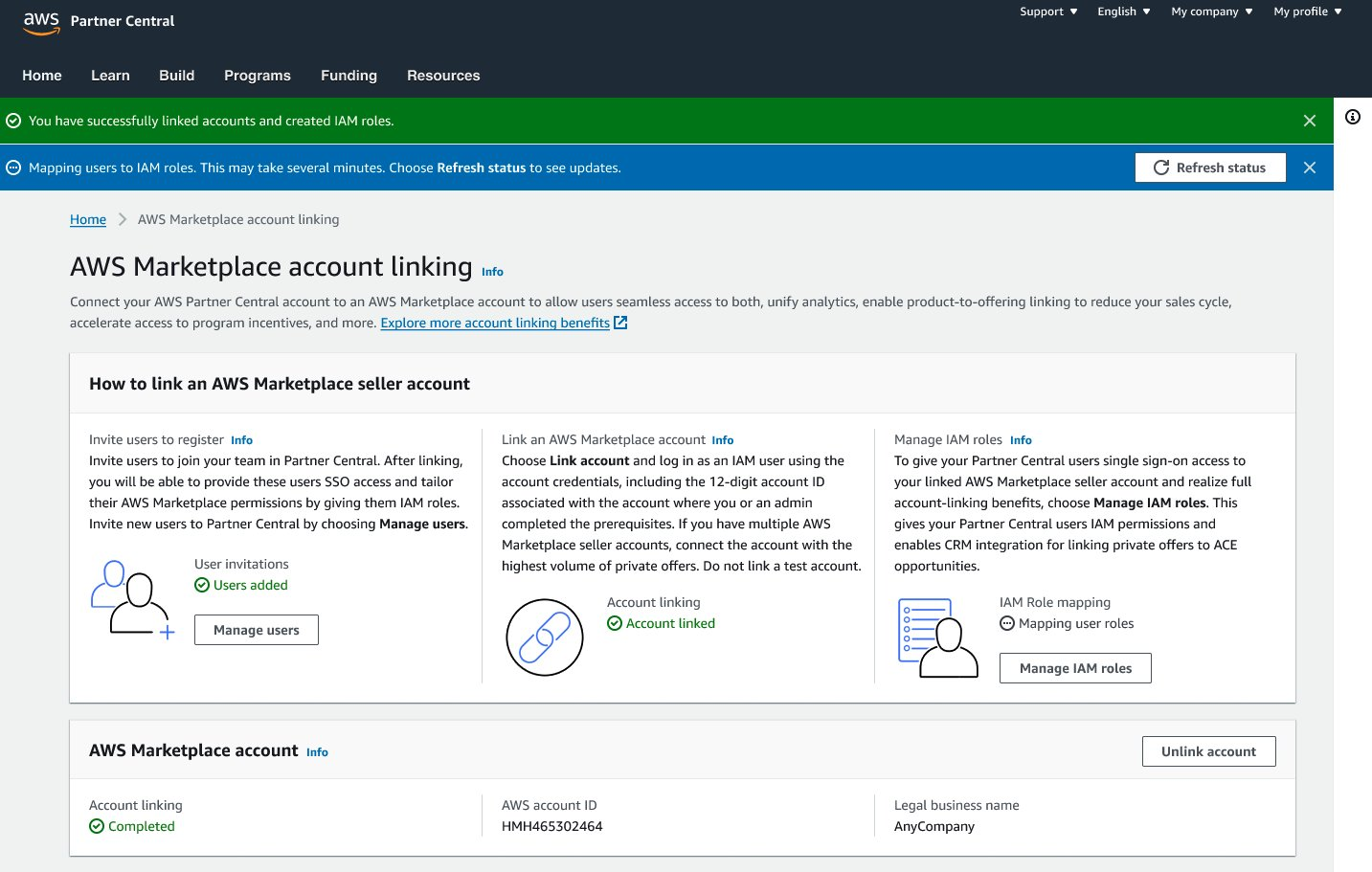
Step 7. Verify Linking Status
- Verify account linking status is green and states Completed under both sections.
- Click on Refresh status button to see updates on IAM roles mapping progress.
2. Configure Integration in Suger
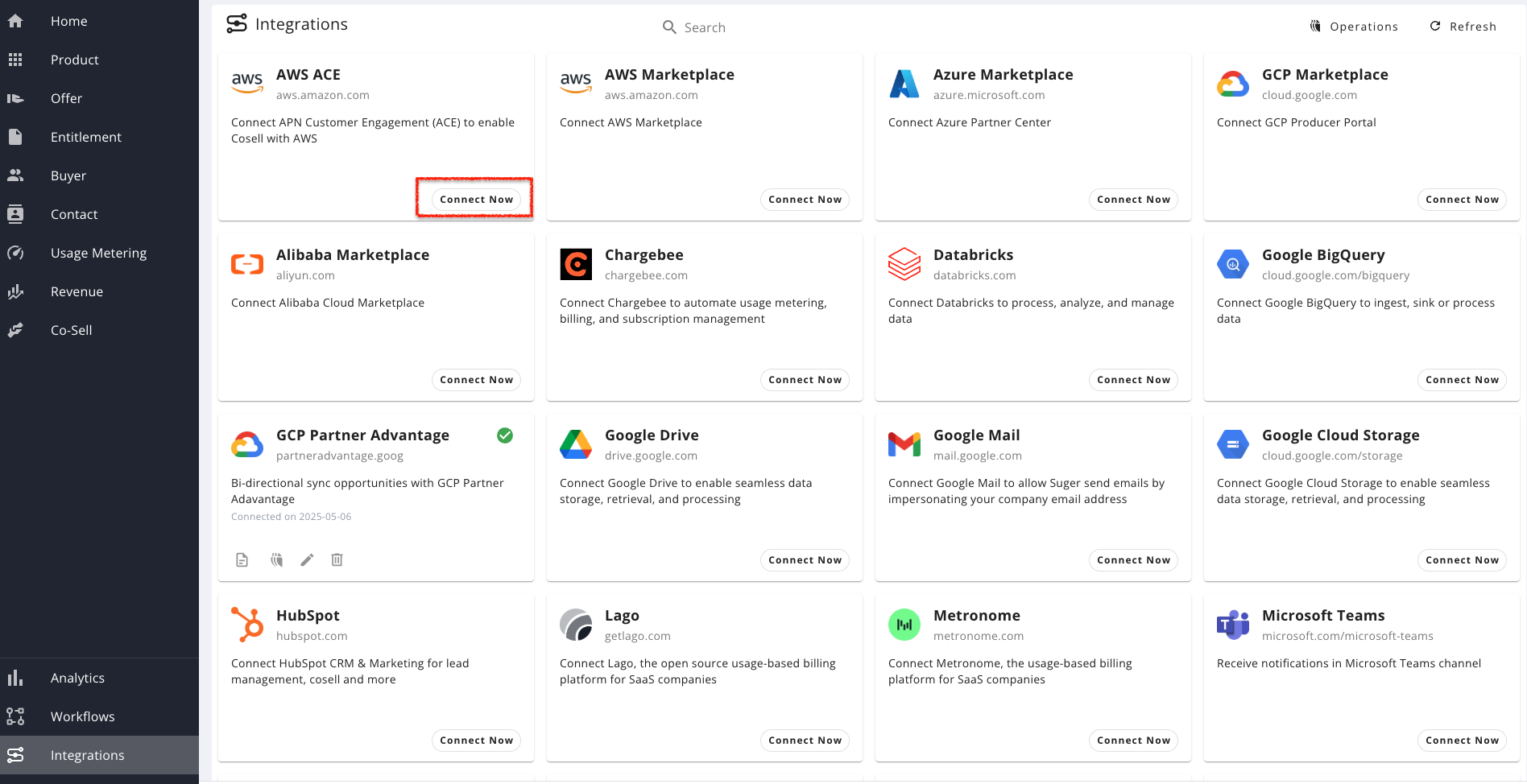
Step 1. Access the Suger Integrations page
- In the Suger Console, go to Integrations → AWS ACE.
- Click Connect Now on the AWS ACE card.
Step 2. Create IAM role via CloudFormation
- Click Create IAM role via CloudFormation. You will be redirected to CloudFormation in the linked AWS seller account.
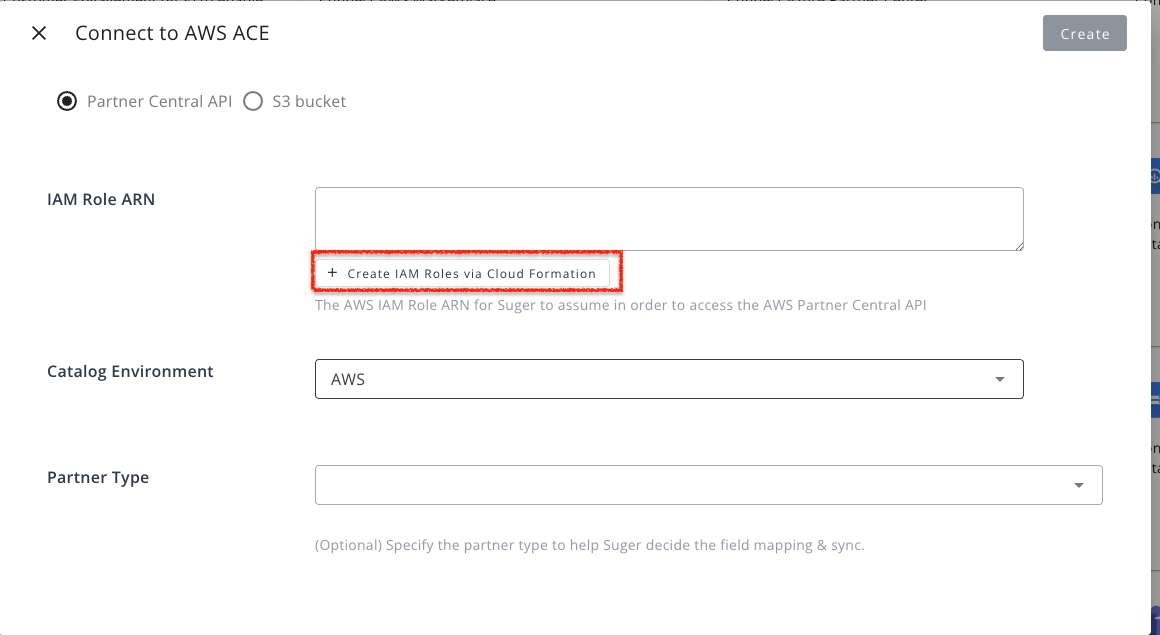
- Sign in with AWS account ID along with its IAM user name, and Password.
info
If your organization uses single sign-on (SSO), use those credentials to sign in to your AWS account first, then sign in to AWS Partner Central.
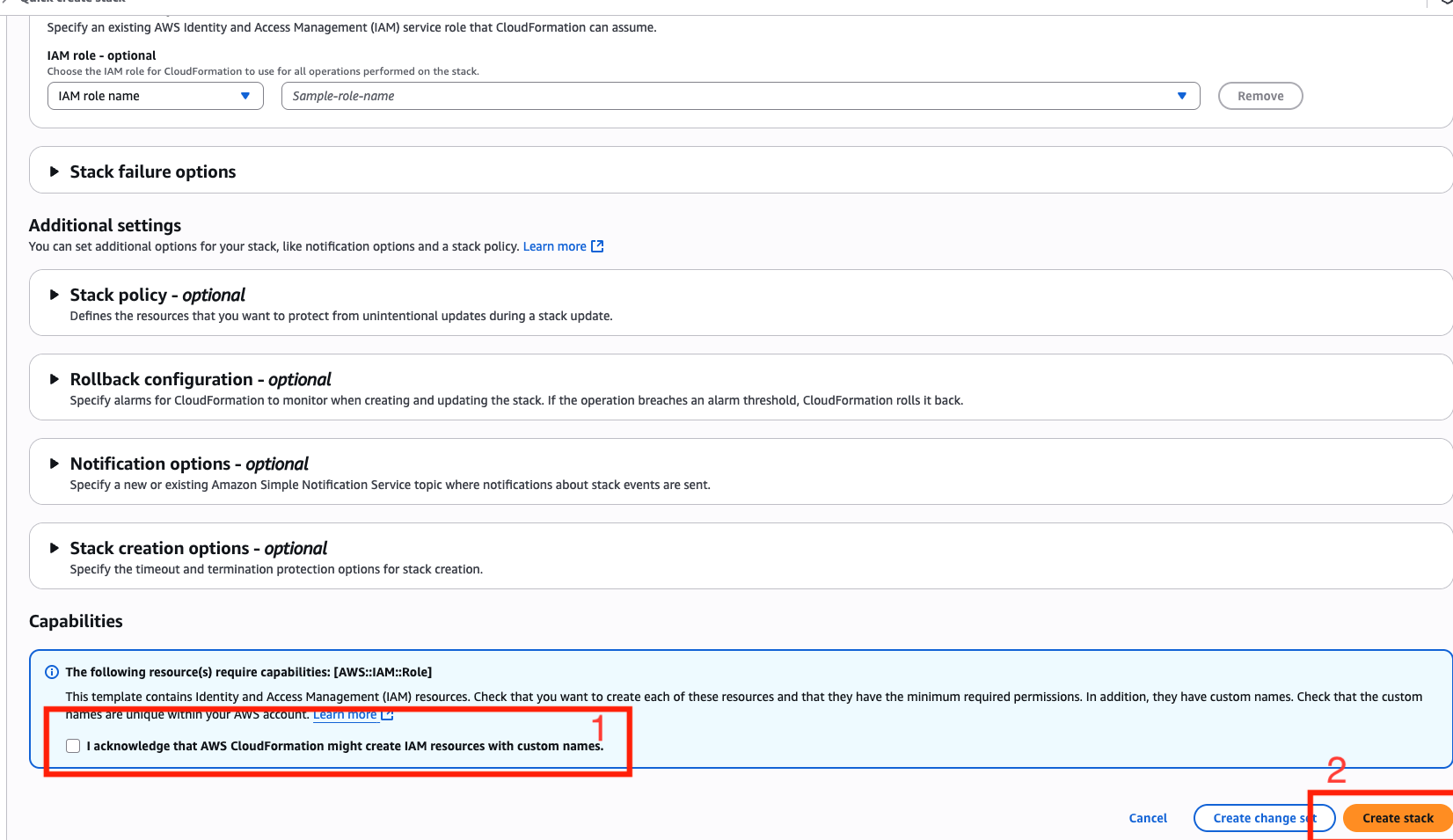
- Check the acknowledgment box and click Create Stack. All required fields are pre-populated.
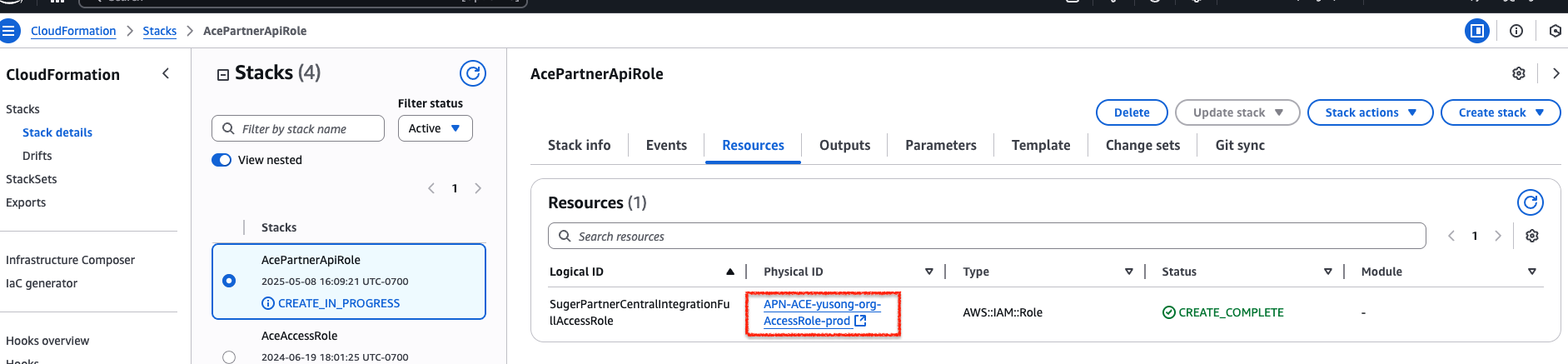
Step 3. Verify the IAM Role Policies
- Find the created IAM role under the Resources tab or by navigating to IAM → Roles.
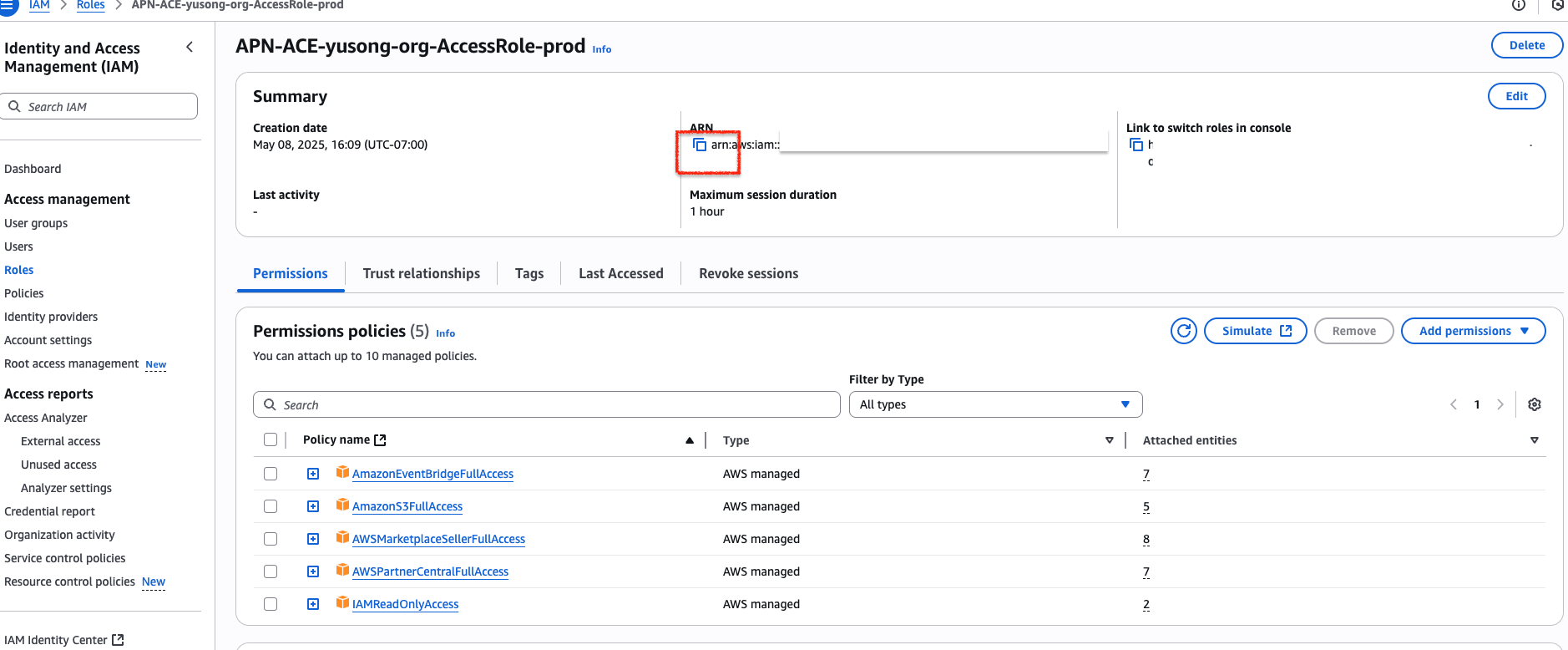
- The IAM role is automatically created with these AWS managed policies:
AmazonEventBridgeFullAccess&IAMReadOnlyAccess: allow EventBridge rules and webhooks for APN opportunity changes.AmazonS3FullAccess: optional, for S3-bucket-based integration.AWSMarketplaceSellerFullAccess&AWSPartnerCentralFullAccess: enable linking APN opportunities with Marketplace private offers and Marketplace product listings.
Step 4. Connect IAM role to Suger
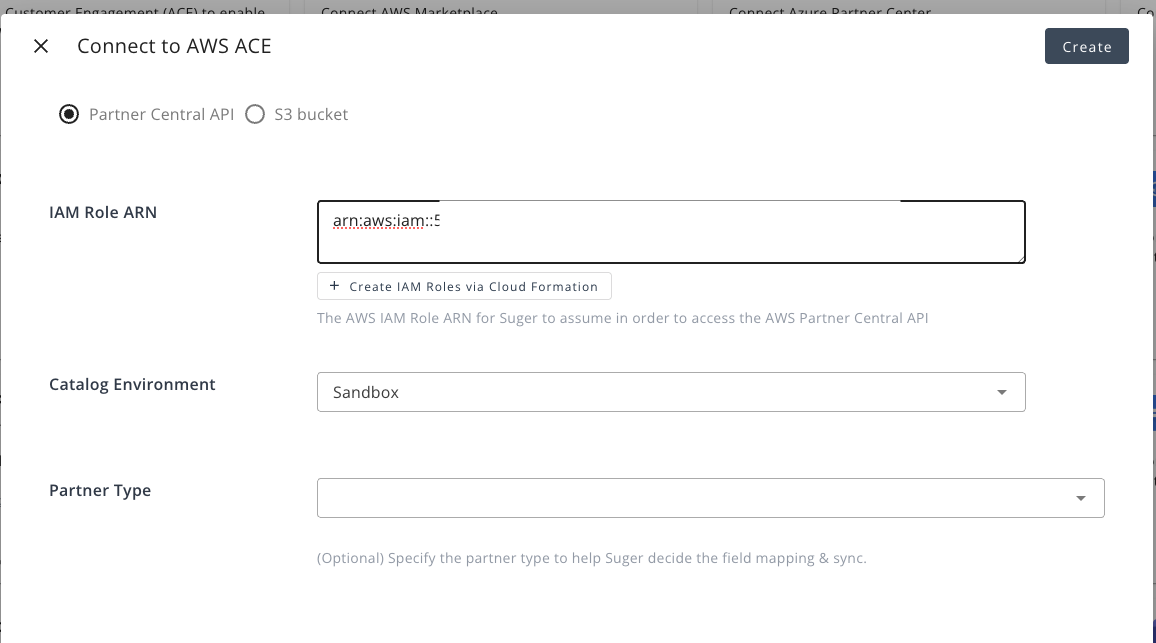
- Copy the ARN of the generated role.
- Paste it into the Integration IAM Role ARN field in Suger.
- Click Create.
Step 5. Verify integration
- Click Verify in Suger.
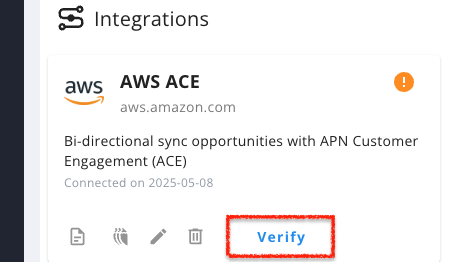
- When verification succeeds, the status will show Connected.
Once verified, the system will automatically create an EventBridge rule and an API destination in your AWS account to listen for APN opportunity changes.
Verification ensures that your IAM role and API connection are working correctly before moving on to data synchronization.
Step 6. Perform Data Synchronization
-
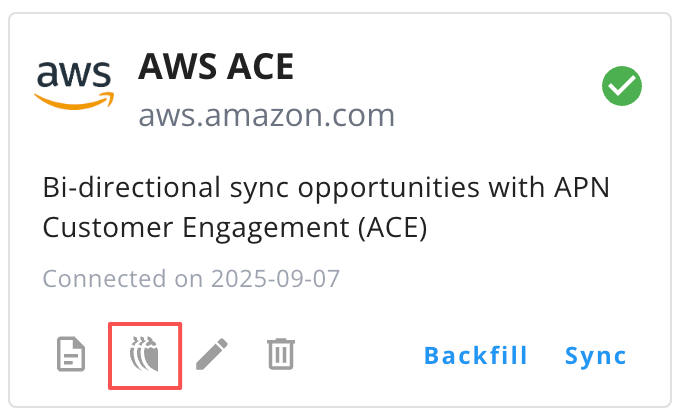
In the Suger Console → Co-Sell → AWS ACE, click the Inbound Sync button to pull opportunity data from APN into Suger.
-
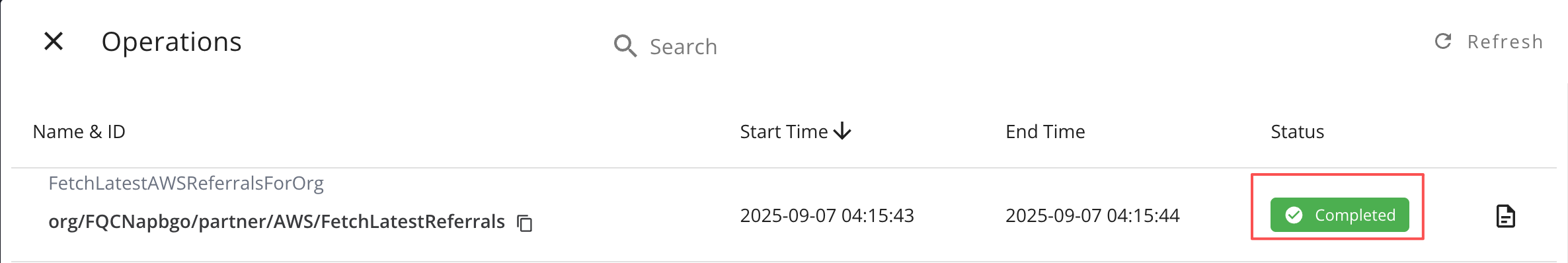
Go to Settings → Integrations → AWS ACE → Operations and wait until the inbound sync status changes to Completed.
DurationThis typically takes a few minutes; the actual duration depends on the number of APN opportunities being fetched.
 info
infoThis confirms the data has been synchronized successfully.
-
Now you are all set!
Delete Integration
To delete the integration, simply click the 🗑️ button in the Integrations list. Once the deletion is triggered, all integration information, including the access token, will be immediately and permanently deleted from Suger.
Please note: once deleted, integration data cannot be recovered.