Account
Manage user, organization & RBAC in Suger Console.
Signup & Login
- Suger use Auth0 as the authentication & authorization provider. Both
Sign inandSign upshare the same entry https://console.suger.io/login.
Standard Login (Email and Password)
Follow these steps if you have a registered Suger account with an email and password.
-
Email Address: Enter the email address associated with your Suger Console account.
-
Password: Type your password.
-
Complete Login: Once both fields are filled, click the "Continue" button to proceed to your account dashboard.
Alternative Login Options
Suger supports sso with Google, Microsoft and OKTA (available upon request). If you need sso with other identity providers like OKTA, please contact us support@suger.io.
-
Continue with Google: Click the "Continue with Google" button to sign in instantly using your existing Google account credentials.
-
Continue with Microsoft: Click the "Continue with Microsoft" button to sign in using your existing Microsoft account credentials.
Creating a New Account
If you are a new user and do not yet have an account:
-
On the login form, look for the text "Don't have an account?"
-
Click the Sign up button
This will direct you to the registration page where you can create your new account credentials.
Password Management and Security
If you cannot remember your password:
-
Click the "Forgot password?" link located above the Continue button.
-
Follow the on-screen prompts to initiate the password reset process.
Organization
-
All Suger resources are organized & managed under organization. Each user must belong to at least one organization.
-
When you sign up for Suger for the first time, you will be prompted to create a new organization. However, please note that your organization will require approval from Suger in order to become active. To initiate the approval process for your newly created organization, please get in touch with Suger Support.
-
The user who creates the organization has the
ADMINrole as default. It is allowed to add new users, edit user role or delete the users. There are 3 predefined standard roles:ADMIN,EDITOR&VIEWER. Their permission scope is defined below:User Role RBAC Permissions ADMINFull access, including management of users, organizations, API Client & Webhook. EDITORFull access, but excluding the access to management of users, organizations, API Client & Webhook. VIEWERCan only access Suger services with readaccess, no permission tocreate/edit/deleteany resourcestip- The
email domainof the organization inherits from the user who created it. - For security purpose, only the users who has the same
email domainas the organization can be added to that organization.
- The
Custom Role with Granular Permissions
Custom roles offer precise control over permissions, allowing you to go beyond the limitations of predefined standard roles, which may be overly broad. This flexibility enables assigning specific permissions at a more granular level.
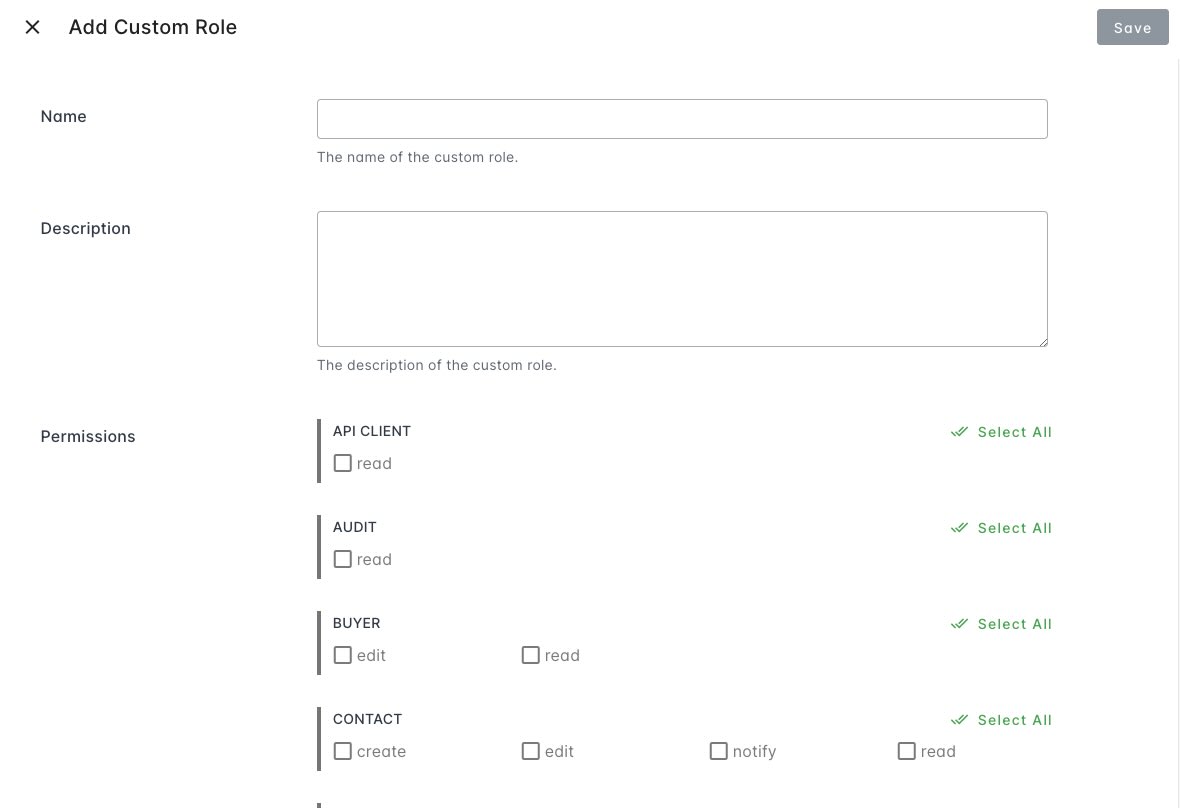
Create Custom Role
- Navigate to the settings page of your organization.
- Locate the
Rolessection under theOrganization & Userstab. - Click the
Add Custom Rolebutton. - Fill in the name and description fields.
- Set permissions according to your specific requirements.
Assign Custom Role to User
Once custom roles are created, you can apply them during the creation or modification of a user.
- Visit the settings page of your organization.
- Find the
Userssection under theOrganization & Userstab. - Add a new user by clicking the
Add Userbutton or edit an existing user by clicking the edit button in each user row. - Set the role field in the
Add User/Edit Userdialog to the desired custom role.
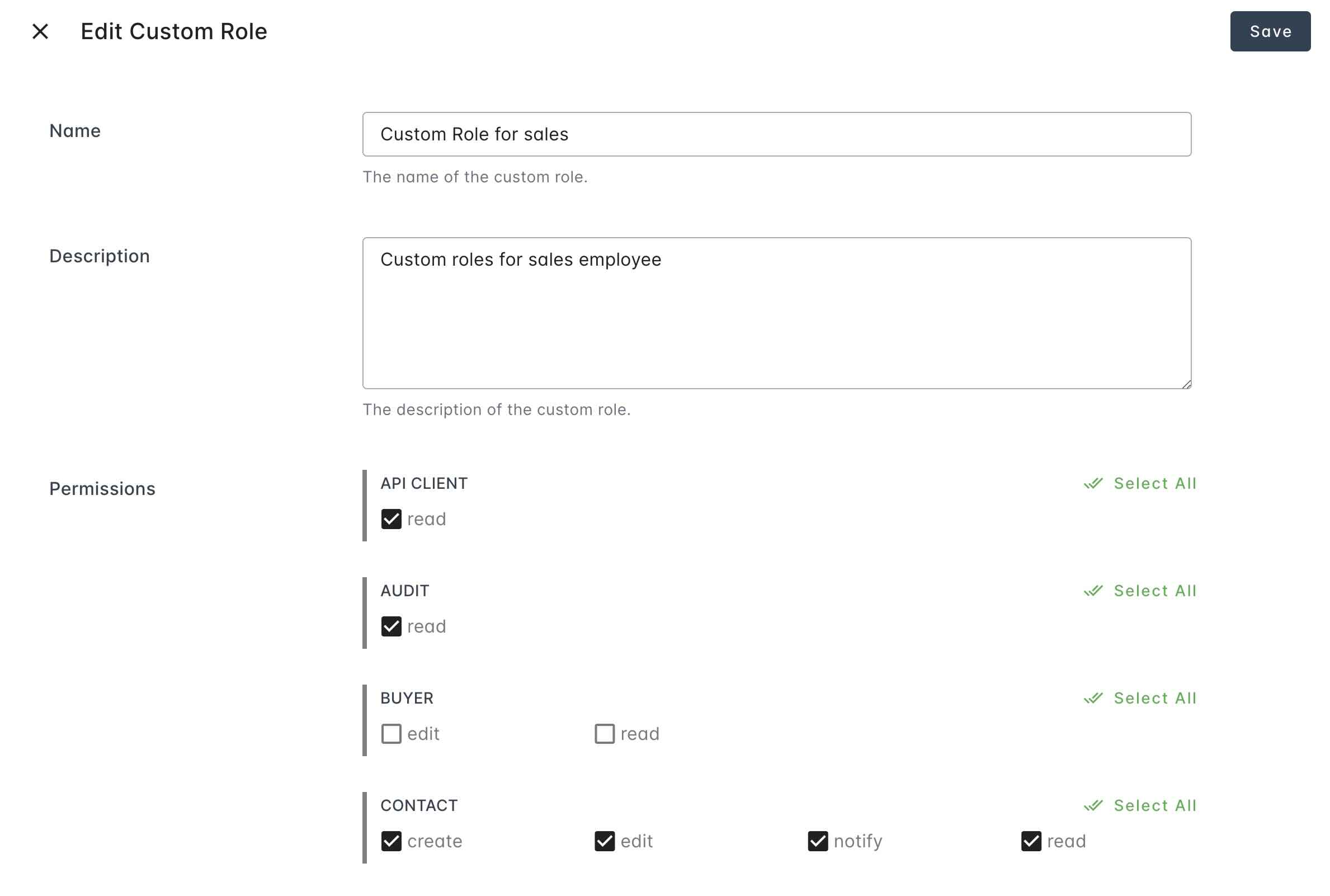
Edit Custom Role
-
Visit the settings page of your organization.
-
Locate the
Rolessection under theOrganization & Userstab. -
Click the edit button in each custom role row.
-
Modify the name, description, and permissions as needed.
Use Okta as Identity Provider
Suger supports Okta as an identity provider, allowing centralized user authentication and access management through your Okta account.
Refer to Okta SSO for more details.